If an attacker gets domain user level permissions they could use tools such as certipy-ad or Certify to enumerate AD CS misconfigurations. Vulnerabilities such as ESC 8 can lead to quick domain ownage. Tools such as ntlmrelay can be used to relay authentication over HTTP and request a certificate on behalf of the victim which can be used for impersonation.
There is a great powershell tool called PSPKIAudit which is available to install and run against your environment.
ESC 1
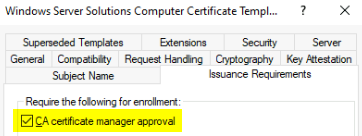
In addition to PSPKIAudit, this powershell command will help detect AD CS templates that are vulnerable to ESC 1. If you have any of these templates issued such as Windows Server Solutions Template or Offline Router you may want to delete them if not used or fix the template. For instance, you could set the Windows Server Solutions template to approval only.
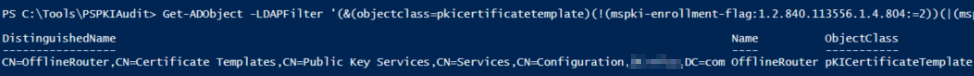
Get-ADObject -LDAPFilter ‘(&(objectclass=pkicertificatetemplate)(!(mspki-enrollment-flag:1.2.840.113556.1.4.804:=2))(|(mspki-ra-signature=0)(!(mspki-ra-signature=*)))(|(pkiextendedkeyusage=1.3.6.1.4.1.311.20.2.2)(pkiextendedkeyusage=1.3.6.1.5.5.7.3.2) (pkiextendedkeyusage=1.3.6.1.5.2.3.4))(mspki-certificate-name-flag:1.2.840.113556.1.4.804:=1))’ -SearchBase ‘CN=Configuration,DC=Domain,DC=com’
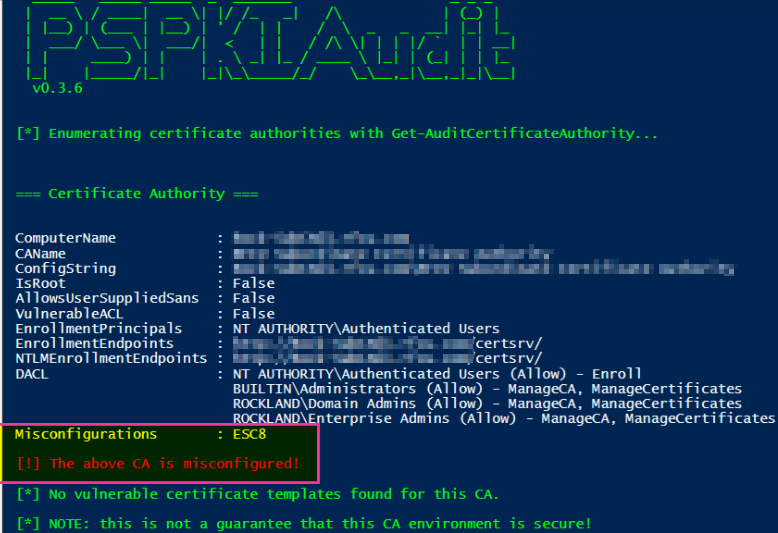
ESC 8
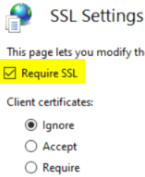
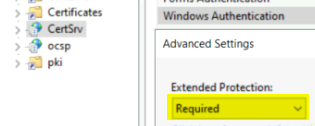
If you are running web enrollment in your PKI and are using HTTP on your CertSrv website, Then you’re most likely vulnerable to this. You can fix this by enabling SSL/TLS and or EAP in IIS. You can also change the authentication from NTLM/Negotiate to something else such as Negotiate:Kerberos. Changing the providers may break your web enrollment. Testing would need to be performed after changing the providers to verify.
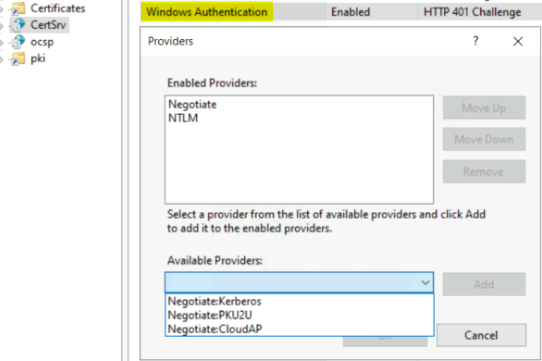
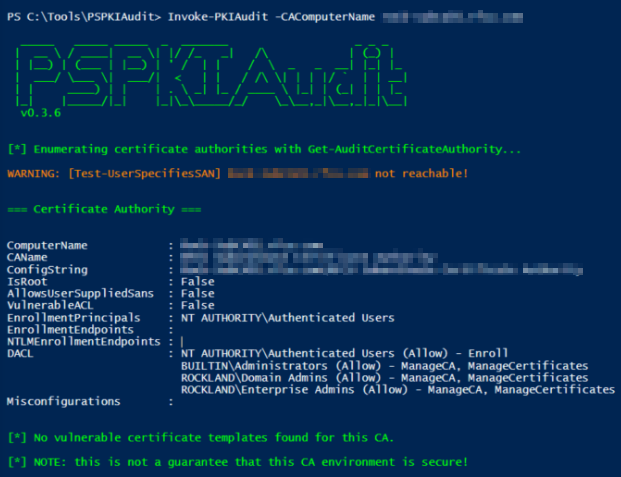
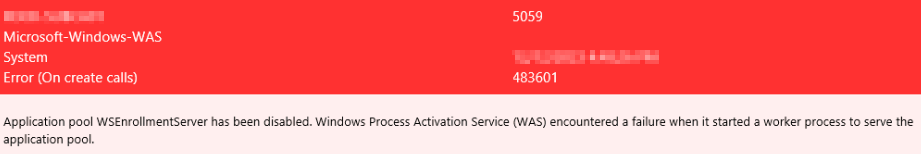
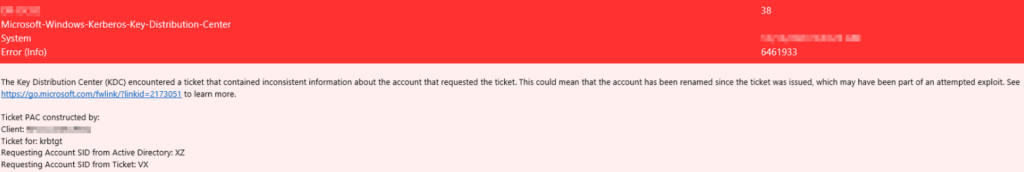
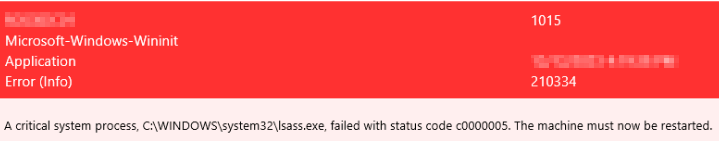
Proper auditing should be enabled on AD CS
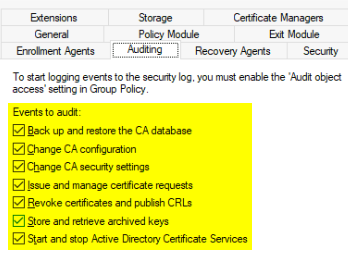
and if you see any of these alerts then you should investigate immediately.