You may have seen this vulnerability pop in Nessus. In order to remediate this we will need to block ICMP type 13 inbound to our boxes.
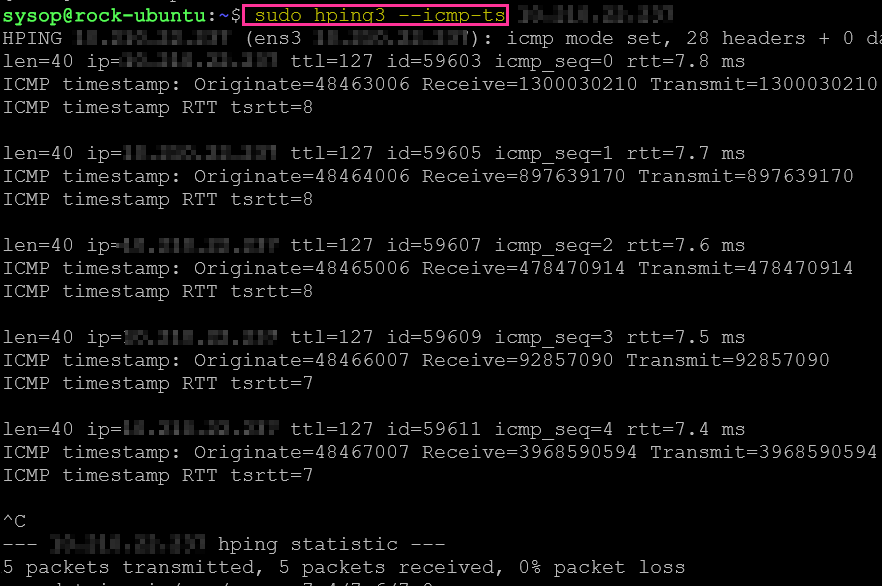
To test this we can use the hping3 tool. Hping3 documentation states you can test for this ICMP type with the –icmp-ts command. In the screen shot you can see the IP responding to Type 13 requests.
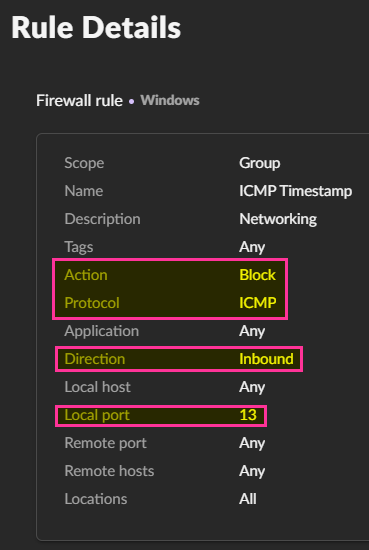
I will be creating a firewall rule in my EDR software (which controls the Windows firewall) to block this. This can be done with any host based firewall software.
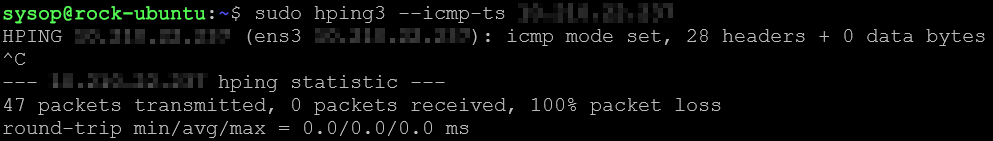
After the host based firewall rule has been set:
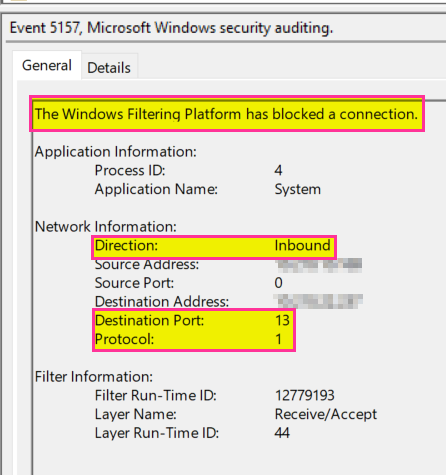
I have Windows auditing enabled for EventID 5157. We can now verify this is blocked.